Here's an example of using PFC on the cmdline. Suppose we get a complaint about somebody who is purportedly IP scanning using TCP. We use the easy way out. To look for TCP packets on the host and getting the basic commandline by appending ``&v=1'' to the URL.
The commandline on this occasion comes out to be:
![]()
The output given by the GUI contains a list of all of the users of TCP:
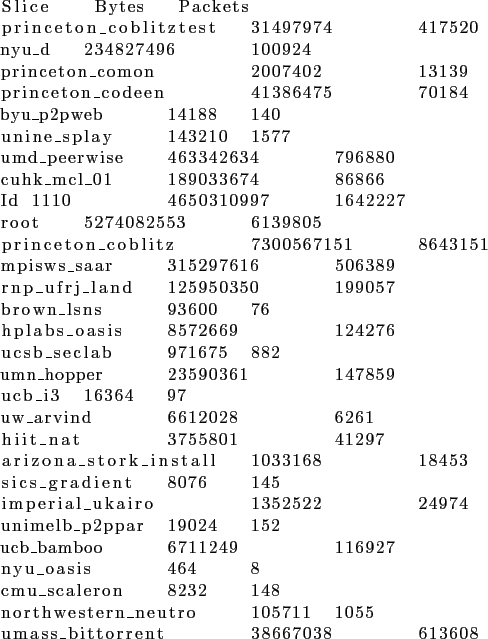
These are not however all scanners. We now modify the line we obtained to add an option that will try to tell the scanners apart from normal TCP users. We specify that the number of packets in the selected flows be less than 2.
![]()
Note the additional -packets 0-2 example. The results are now narrowed down to the following:
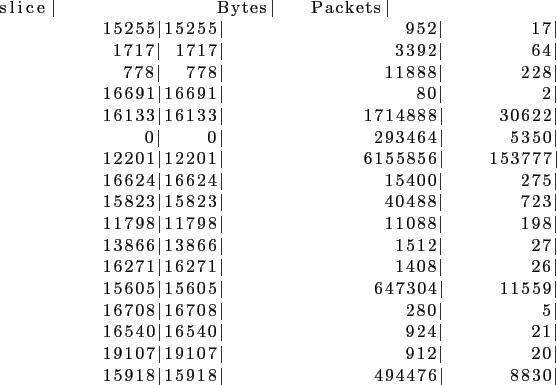
We see in this list a few heavy hitters. In other words, the majority of the traffic can be attributed to two slices: 12201 and 16133, 12201 in particular. Next, we get some statistics on the IP addresses these slices contacted. If the number of IP addresses is large, then it is possible that the traffic in question may involve scans.
![]()
We do so for the slice 12201. Notice that we use some additional options: -slice 12201 to specify which slice we're interested in, and pipe the output to the rwaddrcount command to count the number of IP addresses. Here's the output we get.
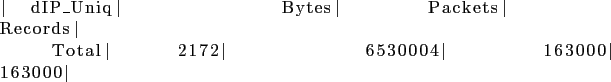
A total of 2172 hosts were contacted by the slice. But are these really scans? We add yet another option: the TCP flags in the packet sent. Also, we drop the packet count to 1 to narrow down even further.
![]()
Notice the -tcp-flags R option for the RST flag. Voila. All of the hosts were contacted using only 1 TCP packet. This is a well known scanning method using TCP. We run one final filter - to find out how many of these hosts are in Planetlab. If most of them are in PlanetLab, then it's probably OK to scan them.

Notice the option -not-dipset planethosts. ``planethosts'' is a binary ipset in a format recognized by rwfilter. It contains a hash table with all of the IP addresses in PlanetLab. This set is created on PFC periodically, but is not part of the PFC distribution. You can create it by calling the GetNodes() method of the PLC API and then invoking rwsetbuild from Silktools. We discover that there is a large number of nodes outside of PlanetLab that have been contacted in this way. So it is almost certainly a scan of external hosts.